Embedded electronic circuits for cryptography, hardware security and true random number generation: an overview - Acosta - 2017 - International Journal of Circuit Theory and Applications - Wiley Online Library

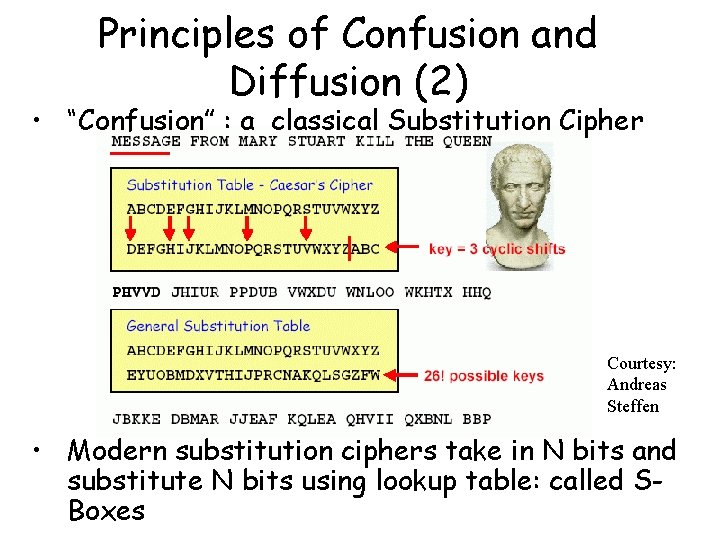
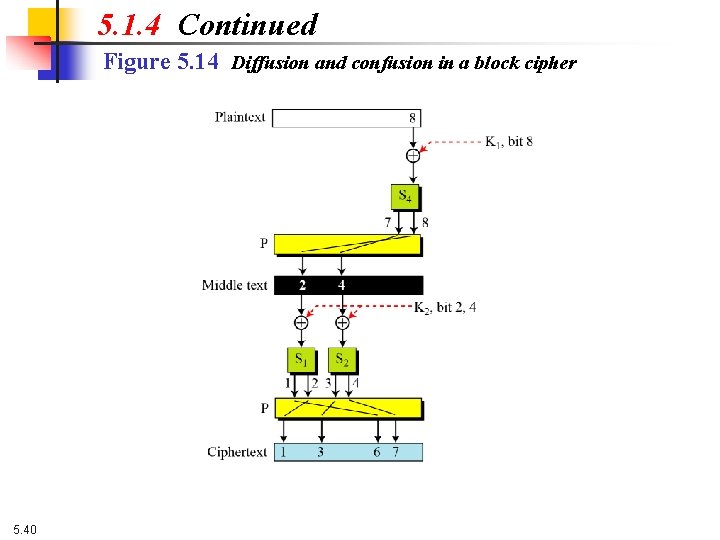
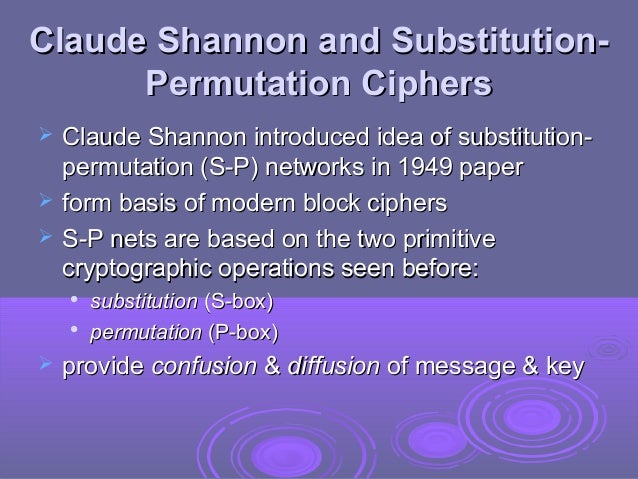
Diffusion and Confusion Two properties that a good cryptosystem should have: Diffusion: change of one character in the plaintext results in several characters. - ppt download

Diffusion and Confusion Two properties that a good cryptosystem should have: Diffusion: change of one character in the plaintext results in several characters. - ppt download

Algebraic techniques on searching linear diffusion layers in block cipher - Zhang - 2016 - Security and Communication Networks - Wiley Online Library